Everything you need to know about Nord's CyberSec feature
You're never fully safe from malware. It doesn't matter if you’re hunting for streams, downloading files, or just browsing. There’s always a risk of catching a virus or falling for a cleverly disguised ad. That may not be pleasant to think about – but there is a solution.
Virtual private networks (VPNs) encrypt your connection and hide your identity online, but that alone does not keep away the hackers. It takes a bulletproof VPN to protect you from malware. NordVPN is one premium service that includes anti-malware protection, thanks to its CyberSec suite.
So what exactly is this feature, how does it work, and should you use it? (Spoiler alert: yes!) We did a deep dive on CyberSec, and below you’ll find all you need to know about the extra layer of protection this VPN offers.
Take a look at our in-depth review to see other reasons why NordVPN is one of the best at keeping you safe online.
Before we get started with CyberSec, let’s take a closer look at malware – not for the timid!
What Is Malware?
Think of malware (malicious software) as a disease for devices. While you may catch it accidentally, it’s often deployed with a sinister goal in mind.
Malware can hijack your device and access your sensitive data. This includes passwords and email lists, credit card info, and even electronic wallets. Those behind it can then use that data to make a profit at your expense.
As you’ll see shortly, malware comes in many shapes and sizes. By taking some control of your device, it can steal or delete your data. It can also spy on your actions as you’re using the infected computer or phone, log your activity, and even change how your device behaves. And while all that happens, you’ll have no idea that your security is compromised. Until it’s too late.
Types of Malware
There’s a huge number of malicious programs out there – enough to leave you very confused. We’ll clear things up with a list of malware types you’re most likely to encounter.
Adware
You probably run into adware several times a day. Short for advertising-supported software, it’s responsible for the pop-up ads you often see on websites or in that “free” app you’ve just downloaded.
While invasive and considered a type of malware, adware isn’t inherently malicious. It’s used as a way to display ads and earn revenue – annoying for many, but not a security risk by itself.
Here’s the problem. Hackers like to pair adware with more dangerous types of malware (such as spyware). This could cause you to click an ad that looks legitimate, only to infect your device with software that can steal your data.
Ransomware
Ransomware was a hot topic in 2016 and 2017, when the notorious Petya and WannaCry attacks happened, but it’s been around much longer. This type of malware aims to hold your device hostage once it’s successfully infected – and the only way out is to pay the ransom.
Usually, ransomware finds its way to your device when you run an infected file downloaded from a shady website, or by exploiting a weakness in network service.
Ransomware is especially dangerous, because it doesn’t care about leeching data from a working system. Instead, your computer becomes unusable until you comply with the hacker’s demands. This makes it very hard, if not impossible, to find a solution once you’ve been attacked.
Spyware
Spyware is all about monitoring your activity without you ever suspecting anything. Unlike ransomware, this type of malware is designed to be as subtle as possible. That doesn’t make it any less harmful.
Spyware has two objectives – to harvest your data (including accounts, login info, banking details) and collect your keystrokes (also known as keylogging). Advanced versions of spyware can even modify the security settings of your applications, leaving backdoors for more attacks.
You don’t even need to visit shady sites to end up with spyware. It often disguises itself in legitimate official software. Spyware is regularly bundled with Trojan horse malware.
Botnet
A botnet is a network of computers infected with malicious bots – programs designed to carry out specific operations. The owner of a botnet manages this network via “command and control” software.
Once your computer becomes part of the botnet army, it can be used for distributed denial-of-service (DDoS) attacks, spam, and even spreading malware. A botnet can also be used to increase ad revenue on websites by visiting them against your will. Last but not least, your internet bandwidth may be shared in a botnet without your agreement.
Botnets are one of the main reasons for CAPTCHA codes, used to verify whether a human or robot is trying to access websites.
Trojan Horse
You’ve probably heard of a Trojan horse, or simply “Trojan,” before. But are you aware of the damage it can cause?
Trojans grant the attacker remote access to your computer. From there, your machine becomes a hackers' playground. They can steal data, modify crucial files, add more malware, and hide their tracks by making their online activity anonymous. They can also hijack the computer and use it in botnets, or observe your activity via spyware.
Fortunately, Trojans don’t spread by infecting other files on your system, and they don’t self-replicate. The most common ways of catching a Trojan horse are by opening a compromised email attachment or running an infected file.
How NordVPN CyberSec Protects You
Did you notice the common thread in the malware types? Visiting suspicious websites makes you susceptible to an attack. NordVPN CyberSec takes care of that problem ahead of time.
CyberSec uses popular lists of blocked websites to identify potential malware threats during your browsing sessions. It scans web addresses you enter against these lists – if there’s a match, access to the website is blocked before you connect to it. That way, you won’t open any websites that are known for hosting malware and infected files.
In addition, CyberSec works to protect you even if malware has already made it to your device. If you’re an unfortunate (and unaware) participant in a botnet, CyberSec will stop the connection between the malicious owner and your device, preventing it from engaging in DDoS attacks and other unwanted activity.
Finally, CyberSec addresses the adware issue with its built-in ad blocker. You won’t have to deal with potentially dangerous pop-up ads or autoplaying videos. An added bonus is the faster loading times on websites with tons of ads.
Our mobile testing revealed that CyberSec significantly reduced our data usage by eliminating all the pop-up ads, making it an essential tool if you're operating with limited bandwidth!
How NordVPN CyberSec Works
Here’s how NordVPN CyberSec protects you from malware attacks. When you type a website’s name in your browser, a domain name system (DNS) request is sent. CyberSec quickly checks whether the request is for a website listed as a threat. If the CyberSec feature doesn’t detect anything dangerous, it allows you to connect to the website. If, however, the website is present on a blocklist, access will be restricted and a warning message will appear.
You can enable CyberSec in just a couple of clicks. Simply open the Settings tab in your NordVPN and turn the feature on! Keep in mind you’ll need an active VPN connection for CyberSec to work:
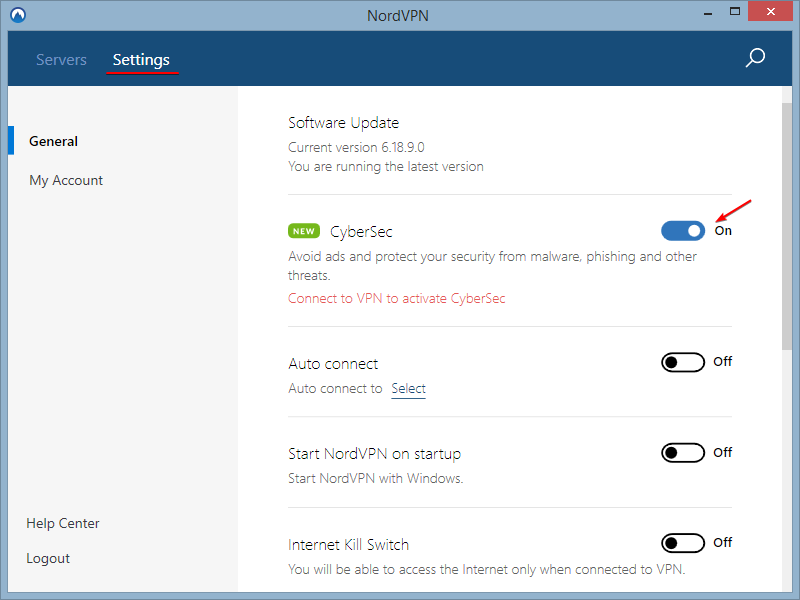
How to Get NordVPN CyberSec
CyberSec comes with every NordVPN subscription. You don’t need to choose it as an optional feature or pay anything extra. This is a huge plus, but we’d expect nothing less from one of the best security-oriented VPNs around.
Other standard NordVPN security features include two kill switches (internet and per app), custom DNS settings to prevent VPN leaks, and special anti-DDoS servers.
CyberSec is currently available on Windows, macOS, and Linux. Android users can also get this feature by downloading the app directly from the NordVPN website.
Conclusion: Should You Get NordVPN CyberSec?
The answer is, absolutely. But there’s always room for improvement.
In the future, we’d like to see more depth to this feature – such as independent settings for protection against malware, DDoS, and ads. More user-side options for blacklisting websites would be appreciated as well. If you want to shop around for VPNs that come with malware protection, both CyberGhost and Private Internet Access have similar built-in features.
That said, CyberSec deserves praise for what it is – a one-step solution to malware's serious threats. This feature is especially useful if you aren’t a tech expert, but because it works quickly, quietly, and effectively, we suspect it has plenty of fans among advanced users as well.
We hope this CyberSec review helped you! For the full scoop on NordVPN, don’t forget to check out what experts and users have to say.
Editors' Note: Intego, Private Internet Access, Cyberghost and Expressvpn are owned by Kape Technologies, our parent company.
Further Reading
What’s the difference between ransomware, malware, and viruses? Learn how to protect your device with our comprehensive guide.
VPNs aren’t just powerful cybersecurity tools. Here’s how you can use your VPN to unlock streaming sites, speed up your internet connection, and more!
Are you concerned about your online privacy? Check out our recommendations for the best no-log VPNs.
Your data is exposed to the websites you visit!
Your IP Address:
Your Location:
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 49% off.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!